FlareON
The Flare-ON competition is a list of reverse-engineering challenges developed by FireEye.
The 2021 edition is the 8th time the FlareON is being held. It is a very popular competition and finishing it is a very reputable achievement in the ctf subculture.
Let’s have a look at the challenges!
Level 01
Here is a screenshot of the first challenge:
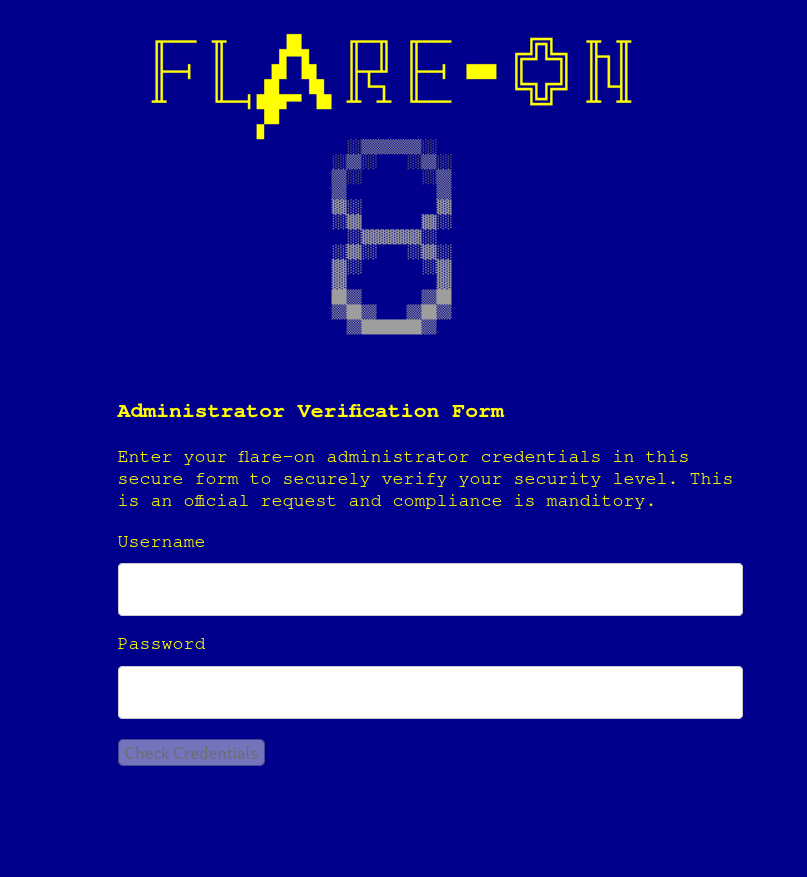
We’re given a prompt to login in some form. The description of the first level states that we should give a look into the javascript to check if there are any credentials stored there.
The javascript is very short, here is a screen of a few lines:
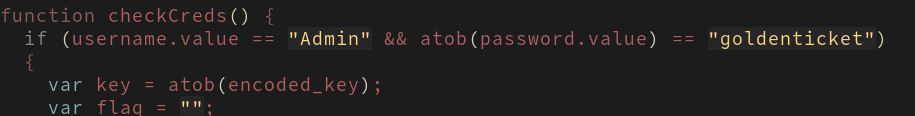
as we can see, the password encoded is goldenticket, transformed through the atob function (which decodes from base64).
So, to recover the password, we just run:
$ echo -n goldenticket | base64
Z29sZGVudGlja2V0
Now using Admin as the user and Z29sZGVudGlja2V0 as the password, we get the following:

Onto the next one!
Level 2
We are presented with a UnlockYourFiles.exe binary, and some encrypted files.
Running the binary will give us the following:
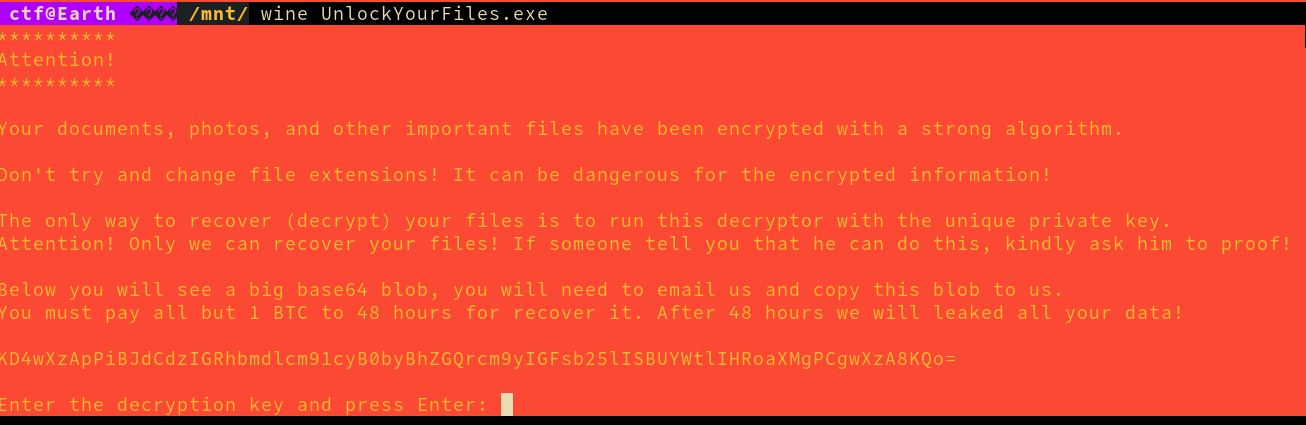
This means we need to reverse the binary to understand how files are encrypted / decrypted.
Let’s first try to decode the base64 “address” to see if it contains any interesting data:
$ echo KD4wXzApPiBJdCdzIGRhbmdlcm91cyB0byBhZGQrcm9yIGFsb25lISBUYWtlIHRoaXMgPCgwXzA8KQo= | base64 -d
(>0_0)> It's dangerous to add+ror alone! Take this <(0_0<)
Well, might be a hint for how the encryption works. Let’s have a look with IDA at the binary. There are only 9 functions, of which only a single one is interesting. Here’s a screenshot of the decompilation:
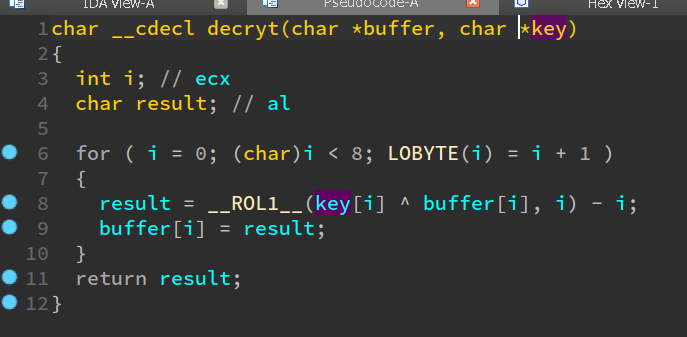
This function is called for each 8 bytes of each file that needs to be decrypted.
As you can see, it does the following steps:
- XOR with a byte of the key
- Rotate left by one, two, three, etc bits depending on which byte it is.
- subtract one, two, three, etc depending on which byte it is.
The decryption routine is quite simple, but we need the key that was used to XOR the ciphertext
with.
Luckily, we can recover the key from the fact that we can infer the plaintext from some of the encrypted files that are provided to us. Here’s the list of files we’re provided with:
.rw-r--r-- 26 root 07-22 19:20 latin_alphabet.txt.encrypted
.rw-r--r-- 49k root 07-22 19:20 commandovm.gif.encrypted
.rw-r--r-- 64 root 07-22 19:20 critical_data.txt.encrypted
.rw-r--r-- 1.7k root 07-22 19:20 cicero.txt.encrypted
.rw-r--r-- 27k root 07-22 19:20 flarevm.jpg.encrypted
.rw-r--r-- 11k root 07-23 02:29 capa.png.encrypted
With a small bit of guessing involved, we can infer that
latin_alphabet.txt.encrypted, when decrypted, contains the text
ABCDEFGHIJKL... (well actually I wasted quite some time because I thought it
was lowercase abcdefghi...).
To get the key back, we just need to follow the steps for decryption in reverse order:
- Add one, two, three, depending on the byte.
- Rotate right by one, two, three…
- XOR with
abcde...
To achieve this, I coded the following C script that also is able to decrypt files:
#include <stdio.h>
#include <stdlib.h>
char key[9] = {0};
unsigned char ror(unsigned char v, unsigned int bits) {
return (v>>bits) | (v<<(8 - bits));
}
char rol(unsigned char value, int shift) {
return (value << shift) | (value >> (8 - shift));
}
void decrypt(char* fname) {
FILE* f = fopen(fname, "r");
while (1) {
char buf[9] = {0};
if (!fread(buf, 8, 1, f)) break;
for (int i = 0; i < 8; i++)
buf[i] = rol((buf[i]^key[i]), i) - i;
printf("%s\n", buf);
}
}
int main() {
char buf[8];
FILE* f = fopen("latin_alphabet.txt.encrypted", "r");
fread(buf, 8, 1, f);
for (int i = 0; i < 8; i++) {
key[i] = buf[i] ^ ror(0x41 + i + i, i);
}
printf("%s\n", key);
decrypt("latin_alphabet.txt.encrypted");
}
Running the above code gives us the key used, No1Trust, and using it to decrypt the file
critical_data.txt gives us the flag:
(>0_0)> You_Have_Awakened_Me_Too_Soon_EXE@flare-on.com <(0_0<)
Level 3
We are presented with an archive which looks an export from a docker image. You can figure this out by looking at the various jsons in the folder and the many references to docker containers and layers.